An Open-Source Improvement for Cybersecurity Content Development

By JUSTIN PRESSLEY
Why Improve Content Development?
Cybersecurity has always been a “cat and mouse” game, but the battle between those seeking to defend their data and those seeking to steal it has never been more savage. Since early 2020, more employees than ever are working remotely – accessing company information via cloud-based servers while sitting comfortably at home.
While this shift has proved convenient for many, it poses significant challenges to the security teams whose job it is to protect this data. Unfortunately, their efforts are made even more complex due to the constantly evolving tactics and techniques used by digital attackers. In many cases, one oversight or lagging methodology can jeopardize the integrity of an entire system.
Like many of you, I have found it particularly difficult to create, deploy, and assess reliable content that allows me to promptly detect these tactics and techniques. All too often, this has left me with a rather difficult choice to make during an engagement: leave a portion of my content untested for its intended use, or reduce the content output which I would typically deliver?
Introducing Attack Range
Splunk’s new detection development platform, Attack Range, provides an open-source solution to cybersecurity. Attack Range functions by emulating the production enterprise environment, allowing you to perform various attack simulations to generate data – data that can then be applied in real-world scenarios. Of course, this provides many benefits to address problems associated with endpoint monitoring, such as:
- It allows the user to quickly build a simulation environment, or “lab,” that functions nearly identically to a production setting.
- Using attack simulating engines like Caldera and Atomic Red Team, the user can create scenarios along ever-evolving lines. This can provide them with the edge they need to tackle new cybersecurity challenges.
- It is easily integrated into almost all (CI/CZ) pipelines, which can help automate the detection process.
Attack Range is a great way to streamline multiple aspects of an attack cycle into one framework. This can allow for faster responsiveness, as well as more reliable countermeasures. And thanks to the platform’s community-based functionality, analysts, researchers, and security personnel alike can all collaborate and share information regarding both potential and past threats.
Clearly, there is a lot of value in allowing analysts to visualize and record offensives, then translate those occurrences into measurable data. Since the environment is merely a simulation, malicious code can be entered into different scenarios while remaining isolated from any actual sensitive data. As a bonus, new, highly accurate lab environments can be created in just a few minutes.
Splunk Attack Range Features
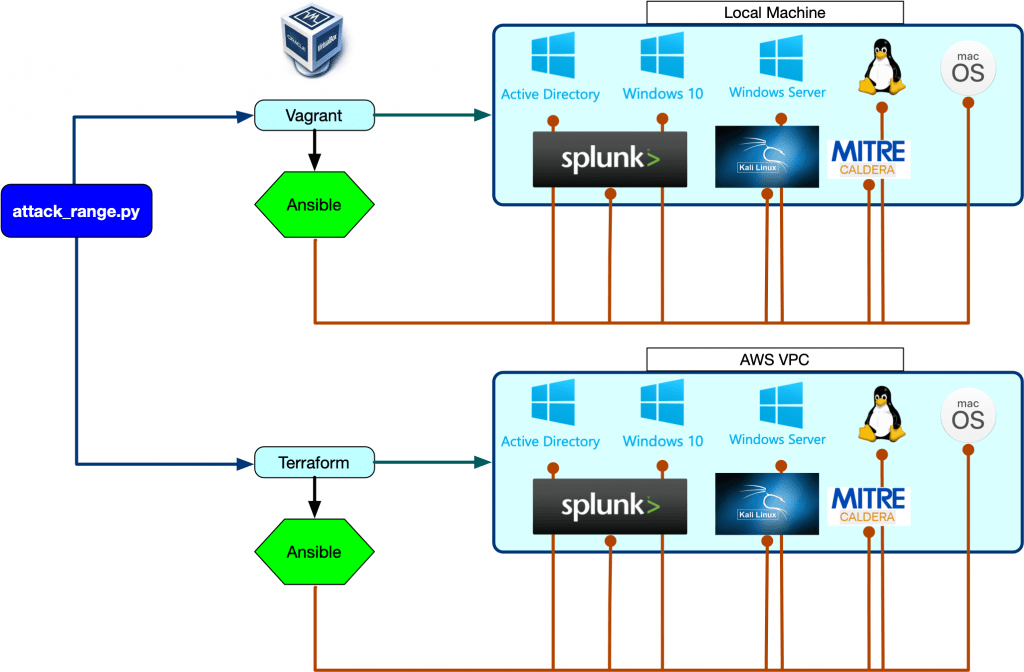
Attack Range’s virtualized deployment consists of a Windows server, a Splunk server, and a Phantom server. It also includes a windows workstation and domain controller, as well as a Kali Machine and Zeek sensor. It is controlled via python and uses rather simple coded commands to perform simulations, dump log data, and construct new lab environments.
Attack Range’s features are comparable to mid-level products on the market and include out-of-the-box detections with Splunk Enterprise Security, a pre-installed machine learning toolkit, and pre-indexed Boss of the SOC (BOTS) datasets. The aforementioned Atomic Red Team attack simulator is included, as is Caldera’s adversary emulation agent. Kali Linux, which is preconfigured for penetration testing, helps round out the overall package.
Users will also have the option to purchase Splunk Enterprise Security, a licensable software that they can use to deflect information attacks that occur during the research phase. All in all, Splunk has put together a pretty impressive open-source platform suite. Most companies will find it perfectly suitable for maintaining their edge in the ongoing cybersecurity war.
The Future of Content Development
This latest version of Attack Range is an expansion of the Attack Range Local Project and now allows environments to be created via cloud providers such as Azure and AWS. In the future, the Splunk team hopes to improve the product by using docker containers to make installation on both Windows and macOS much faster. At the same time, they hope to increase the speed at which valuable attack data can be passed around the community.
With Attack Range, Splunk provides an excellent open-source solution for modern cybersecurity. Leaders in commercial enterprises who feel this product makes sense for them will find it a great way to keep the “mice” on the run.
The second part of this blog will be a demonstration on how to deploy Attack Range. Until then, check out how Concanon uses technology such as AttackIQ or FireEye to validate even more controls than what’s included free with Attack Range. Click here to review our Control Validation methodology.
Start Saving Today with Concanon
Interested in deploying content or Attack Range in your enterprise? Would you like to validate your cybersecurity investment is working as intended? Schedule a free consultation with us today. We can provide you the required experience to ensure you trust your data and the cybersecurity controls used to defend your enterprise.
Concanon's Author
Justin Pressley is a Cybersecurity Consultant for Concanon LLC, building, developing, and leading security tooling. Justin has 10 years of experience in IT and has built cyber ranges and content for some of the largest firms in the U.S. His programming background provides a deeper level of insight in to the required data needed for proper detection of the newest cybersecurity threats.